For individuals with business interests, public profiles and family members to protect, the internet poses bigger risks in terms of reputation management for high net worth clients than ever before. Here, experts in digital security, reputation management and law tell Chris Stokel-Walker how HNWs can mitigate the threat
The couple were happy. They had built an array of successful businesses, they supported a range of charitable causes and they were genuine patrons of the arts. But, preferring privacy to self-promotion, they didn’t like to shout about any of it.
Having secured a heart operation for a child from a developing country, they preferred to focus on the next child they could help, rather than give interviews or issue press releases to broadcast their achievement.
‘They never cared to be known online,’ says Valeriya Melnichuk, a director at advisory firm Highgate. But then – as often happens in families – there was a falling-out, and then a rift. While the couple continued their work, some of their relatives bore a grudge – and decided to take action. They filled the digital void about the family with smear stories – a dark arts PR campaign.
A few negative articles were published about the couple, which they shrugged off. ‘Who cares,’ they reasoned, Melnichuk recalls. ‘We know we’re good people.’ However, the negative PR campaign, waged on the digital battlefield, took its toll.
Banks began probing the couple when they opened new accounts, asking them to explain some of the more troubling claims they found online. They had to jump through hoops to prove the source of their income was legal after banks pointed to Google search results that claimed otherwise.
Beyond a mountain of paperwork and bureaucracy to do everyday things that had previously been normal, there was a more pernicious effect on them. Their children started growing up and were teased at school about scurrilous gossip on social media. They then began asking their parents whether the claims were true – prompting difficult conversations to dispel the lies.
‘The starting point is that everything is online, or can end up online. A lot of HNWs don’t appreciate how they leave information behind’
The campaign ‘didn’t ruin their life’, says Melnichuk. But it became ‘more and more present in their business and personal interactions’. The couple eventually approached Highgate for help. When the firm looked into what was being said online, it found a tangled web of half-truths and supposition damaging their reputation. On the internet, anonymous accounts can say anything – and anything you say can be used against you.
The solution was simple: use positive, genuine stories to drown out the negative lies. Highgate began a reputation management blitz, communicating more clearly all the good things the couple were doing and highlighting their foundation. It enabled the couple – who had always avoided ‘oversharing’ – to tell their own story and crowd out the mistruths. The negative stories were pushed down and out of search results for their name, and the awkward conversations – with bankers and their own children – became a thing of the past.
Of course, such a situation could have been prevented from taking root, had the couple been quicker to accept the realities of modern life for HNWs: if you don’t have a digital presence or profile, someone else will create one for you. But it can be difficult to strike a balance. Talk too little and an information void exists into which disinformation pours. Share too much and you risk tipping off bad actors, who might see an opportunity for ill-gotten gains.
***
If a private detective were following you round as you lived your life, tracking and tailing every shop you entered, every place you visited and every conversation you had, you’d act quickly to stamp it out. But when the same thing happens online, people often ignore it. They shouldn’t.
By one estimate, the internet contains 250 trillion web pages. ‘That is an enormous amount of data,’ says Cameron Colquhoun, who founded corporate intelligence consultancy Neon Century after the best part of a decade at GCHQ, the British government’s intelligence headquarters.
‘Very often people are not targets simply because of their personal history, but because of what they represent,’ says Thomas Eymond-Laritaz, founder and CEO of Highgate. ‘And this is when it’s becoming dangerous – either because they represent wealth, or they represent success, or they represent a certain political orientation.’
It’s therefore vital to consider what this means for the way you live your life. ‘The starting point is that everything is online, or can end up online,’ says Emma Woollcott, head of the reputation protection group at Mishcon de Reya. ‘A lot of high-net-worth individuals don’t appreciate how they leave information behind and that it can be used against them.’ ‘A digital footprint really can represent a pool of sensitive data which could be leveraged against you,’ says Beatrice Giribaldi Groak, partner at Digitalis, a London advisory firm.
It’s something we often forget, because we salami slice the amount of information we give away – a mother’s maiden name on a security question here, a birth year through a username there – without realising it can all be put together like a jigsaw to produce a fuller picture of who you are. ‘There is, at times, a sense of light-heartedness towards how much data there is out there about someone.’ When clients seeking assistance first approach Digitalis, the firm, like many others, will often conduct a digital reputation audit.
Usually the process uncovers an eerily detailed portrait of a person that the person had little idea existed in its totality online. ‘If you know what exists out there on the internet, you’re better informed,’ says Matt Lane, a director and co-founder of X Cyber Group, a cybersecurity firm based in London and Gloucestershire. ‘The more informed you are, the better protected you are.’
Step one is to come to terms with a difficult truth: the internet never forgets. If information is archived somewhere, it’s likely to be accessible to independent researchers, private investigators and journalists. Take the recently uncovered Pandora Papers, a tranche of 12 million documents dating back to the 1970s that was unveiled by a consortium of journalists in October.
Some of the documents revealed details of dubious business practices dating back to a time before the internet really existed in a publicly accessible format. The revelation of the Pandora Papers is an extraordinary event, but corporate intelligence experts often come across similar nuggets of information when conducting routine digital audits for their HNW clients.
‘When we’re doing investigations, often we’ll find things going back to 2002 and 2004,’ says Colquhoun. ‘Nobody can possibly remember all the things that they did back then.’ Those long-forgotten entries somewhere in a database are the riskiest things that can be uncovered when raking through one’s digital traces, says Woollcott. ‘More often than not, if there are sexy images, or compromising images or information, the subject knows about it.
But the thing that is most often unknown is the extent to which [people have] featured in historic data breaches and data thefts.’ The advice, then, is to be cleaner than clean – but that is often easier said than done. ‘We are not able to give clients a time machine and allow them to undo the mistakes they made in the past,’ says Woollcott.
Instead, anyone aware there could be skeletons in their closet can proactively work with companies like Mishcon de Reya to think about how to prepare if certain things were ever to come to light. One’s own actions or past indiscretions are not the only thing to consider.
Pictures posted by other people – family members, acquaintances, support staff – can also prove to be highly useful for those trying to build up a picture of your life, or to understand a little more about your lifestyle, even if the pictures appear perfectly innocuous at first.
A photo taken at a party, for example, can reveal more than you might like – even if you are not in it. An image of your car’s licence plate can be cross-checked against databases to glean more information about your home. A selfie taken by a cleaner in the bathroom mirror of your home can give away the type of locks on your door, aiding a break-in. The family pet’s playful Instagram profile can reveal untold secrets that can all be built up to understand when you will or won’t be at home, walking the dog at the local park.
***
A spate of robberies at the homes of Premier League footballers in the north-west of England has been linked to Instagram posts by the footballers themselves and their families. Glitzy posts showing off a recent jewellery purchase can act as a digital storefront for thieves.
In April 2020, £500,000-worth of items were stolen from the city centre property of Manchester City’s Riyad Mahrez. Among the items stolen were a Rolex Daytona and a Richard Mille watch. It came just months after Mamadou Sakho, who at the time was a Crystal Palace defender, lost £500,000-worth of property when his Wimbledon home was raided by criminals.
Both players had shared pictures and videos of their high-value items with their millions of followers. Instagram posts are just one of many types of what Colquhoun calls ‘data crumbs’, which he says ‘can be huge pivots for us if we’re doing an investigation, or for a hostile party to profile you, track you, or to ruin your reputation’. Sometimes these data crumbs can come from unusual places.
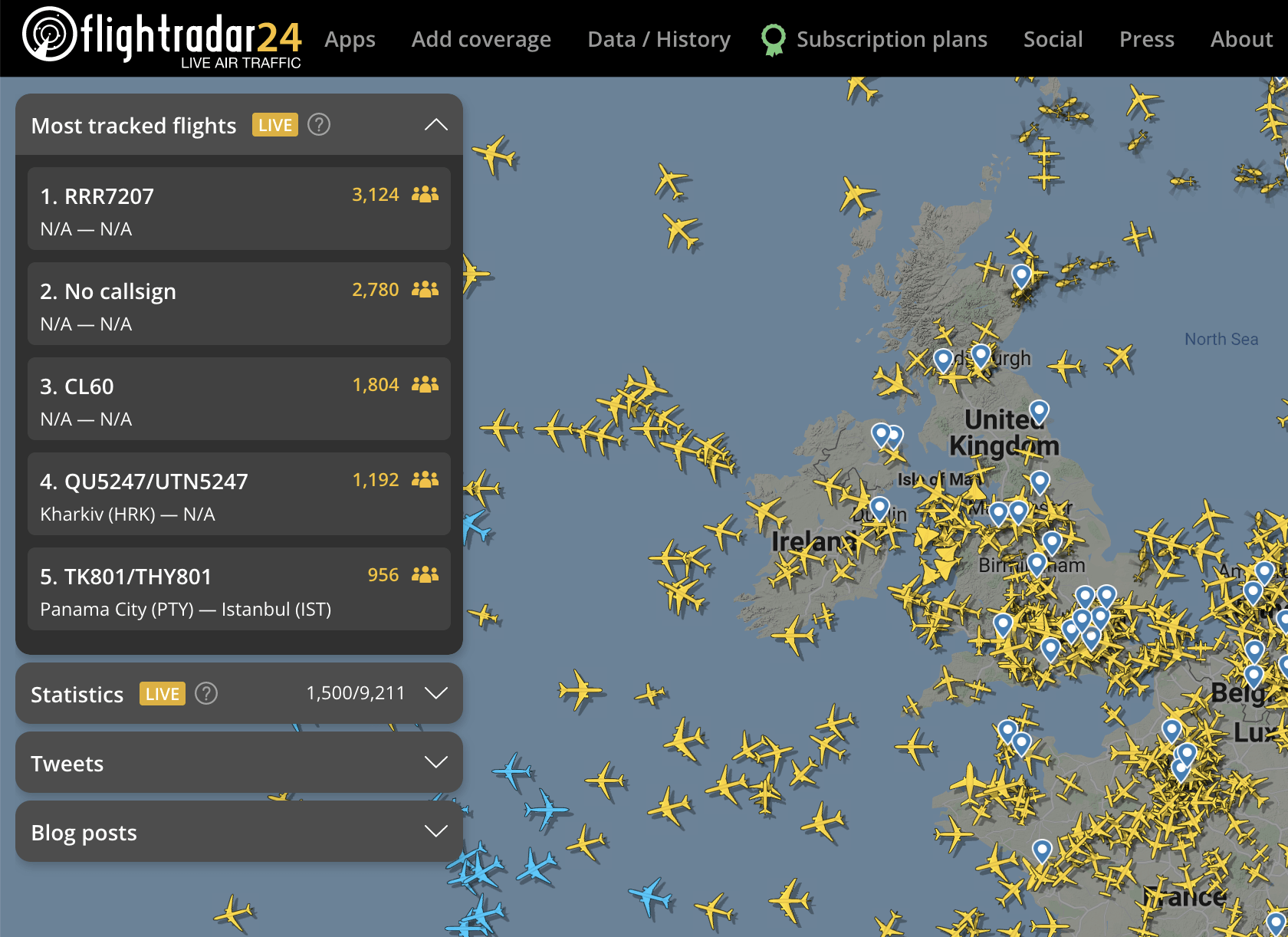
While you may shun scheduled airline flights in favour of chartered planes for convenience and because you believe it’s less public, databases of tail numbers mean it’s possible to track someone’s travel using Osint – open source intelligence – unless they specifically opt out. Several tech billionaires and HNWs are thought to have filed applications to remove the tail numbers of their private planes from tracking databases, but plenty of others can be viewed by all and sundry on sites such as Flightradar24 or Jettrack.
Such information may seem innocuous, but in the rarefied world of UHNWs, knowing where someone is can be like gold dust. Academics have managed to track corporate mergers and acquisitions using the movements of corporate aircraft; traders now look at flight movements to get tip-offs about where the next big trading windfall could come from.
Those who spotted the Gulfstream jet owned by oil company Occidental Petroleum landing at a littleused airport in Omaha, Nebraska in April 2019 could well have put two and two together to conclude that Occidental executives were there to meet Warren Buffett, who lives nearby. Had they done so and put their money into Occidental stock, they could have benefited two days later, when Buffett said he’d be investing $10 billion in Occidental.
***
Even the wives of despots and dictators aren’t immune from being tracked through big data: Dictator Alert, a project that tracks when planes operated by the rulers of authoritarian regimes land at major airports in Paris, London, Geneva or Basel-Mulhouse-Freiburg, keeps its beady eye on the skies.
The tool uses an aircraft’s Automatic Dependent Surveillance-Broadcast (ADS-B) pings, which are used to help air traffic controllers route flights, to see where the world’s ultra-wealthy are travelling. Getting your plane’s ADS-B information delisted from official databases is difficult, and doing so would cut you off from a large part of the world.
The United States, for instance, requires any aircraft in its airspace to broadcast their pings. But you can make it more difficult for would-be sleuths to track you. Publicly available sites like FlightRadar rely on data from the Federal Aviation Administration and other national and international bodies like it. It is possible to lodge a request to be taken off these lists – but it’ll only get you so far.
To avoid prying eyes, there’s only one solution. ‘Fly on normal commercial aircraft,’ advises Colquhoun, with a chuckle. All this information can be used as kompromat, designed and deployed to catch you in a trap, or to learn more about you to prepare for a future attack.
But even HNWs taking all the proper precautions can face digital dangers if a bad actor chooses to launch a whisper campaign through social or digital media, with the aim of damaging someone’s reputation. Anonymous accounts, aided by the use of bots, can seed negative perceptions of a person on social media.
It’s a claim that may seem far-fetched at first, but lawyers acting for Hollywood actor Amber Heard alleged in her counterclaim to a lawsuit filed by Johnny Depp against her that authentic and inauthentic social media accounts, alongside bots, had targeted Heard’s Twitter account.
Given that what’s posted on Twitter can be quickly echoed and amplified, this type of material can serve as kindling for a much larger fire. The solution for HNWs, as it always has been, is to take the high road. But, just as with the philanthropic couple who felt compelled to boast about their charity to fill the void, sometimes you need to engage.
‘Whenever you can stay under the radar, it’s a better position,’ says Eymond-Laritaz. ‘But when you know criticism has been voiced, and it’s only the beginning, you have no choice. You can’t become a collateral victim of a political fight. You have to take action.’ In the drive to take action to protect their reputation, some people unwittingly fall victim to another issue: not every company operating in this space is legitimate.
Many firms that claim to be able to launder a digital reputation are more interested in gaming Google’s algorithms to end up near the top of search results for key terms that might be used by victims of blackmail and digital dark arts campaigns. Sometimes these companies are simply a front for hackers that hunt people whose private information could be exploited through ransomware attacks and other scams.
One terrifyingly common strain, called REvil, reportedly seized the data of Hollywood clients of law firm Grubman Shire Meiselas & Sacks in 2020. The hackers are thought to have asked for $21 million in exchange for not taking the data public. As the digital economy continues to swell, the reputation management industry also continues to grow.
Globally, it’s expanding at 14 per cent a year, according to one estimate. ‘I think there is a greater appreciation of the information that people put out there and more effort has been spent on security, and being a bit more savvy,’ says Woollcott. ‘But humans make mistakes. And often, the adversaries are quite opportunistic. Sometimes they will have a go and see where they can get with things. So I think it is a problem that will continue to crop up.’
The solution, then, is to be proactive. Take control of your digital life. And for goodness’ sake, if you’re an HNW, think twice before you post.
For a comprehensive list of the top reputation managers, visit the Spear’s 500.
Illustration: Madison Ketcham
Read next:
- The Spear’s Reputation Management Index
- The best reputation lawyers for HNWs
- The best reputation managers for HNWs